Welcome!

^ not a lab
homespun CSS and various experiments in on- and offline crafting

^ not a lab
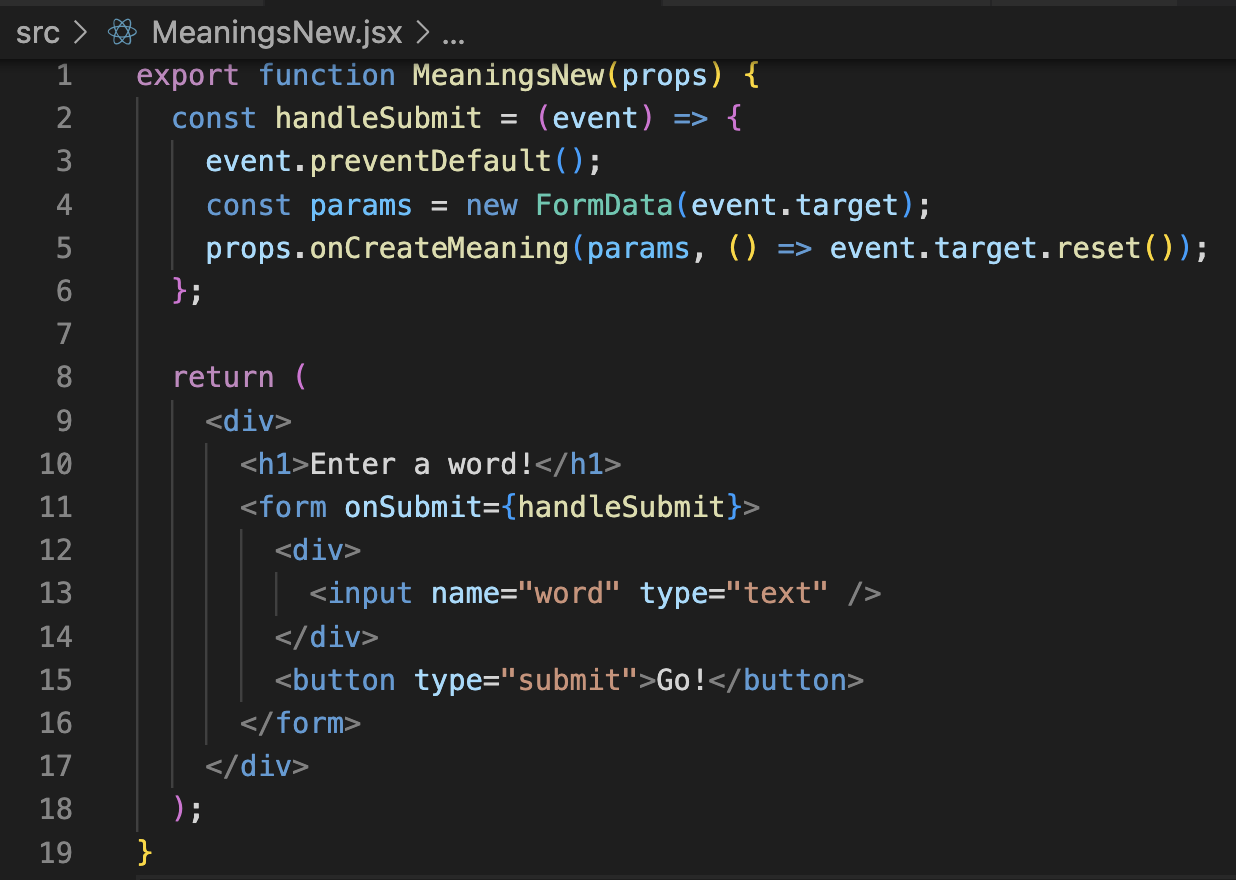
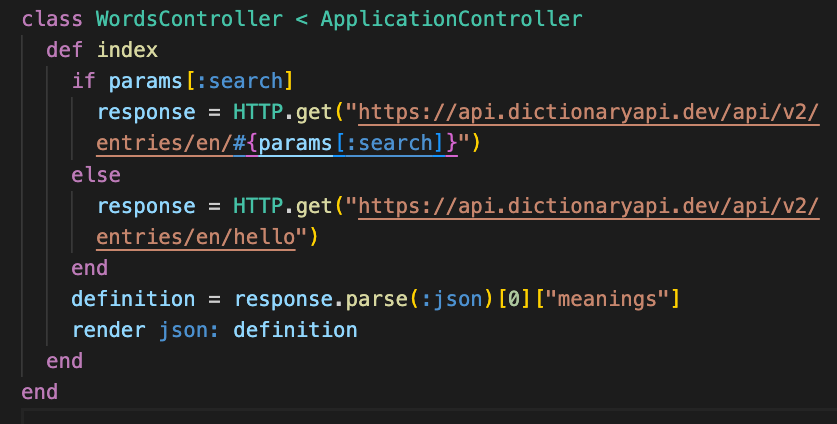
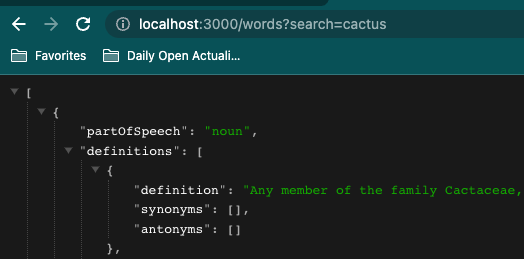
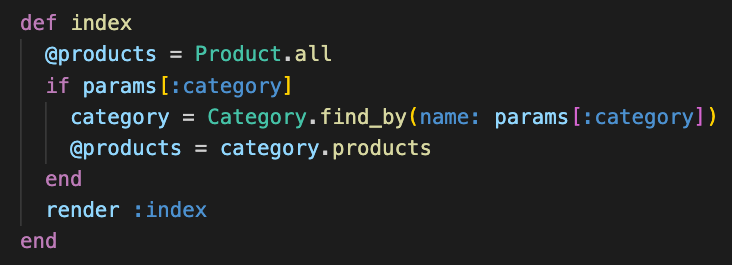
I picked up some supplies to start my first quilt, so that means it's time to tackle building out the frontend for my store. (Which right now only has some amigurumi but that can be changed!) I'm not at all sure how to build out a frontend to work with my cart on the Rails backend - which was a little tricky to create - but I'll just start with the basic CRUD actions first and chip away at it bit by bit!
I ran a reverse image search using Google, Bing, Yandex, and Tin Eye. A Google Lens search showed that the exact photo is being used as the Facebook background picture for Oan Resort, and it's also the main picture on the resort's homepage. I found the resort on Google Maps and pulled the coordinates so I could check it out on Google Earth. Looks like we can confirm the picture is Oan Resort, Micronesia, and the camera was facing NW when the photo was taken.
OSINT Exercise #008A reverse image search yielded nothing, but the translate function on Google Lens worked a charm and clarified that the audience was applauding a Shen Yun performance. Still using Google Lens, I copied the Chinese-language title and subtitle and regenerated the search results. The resulting articles made clear that there were 7 simultaneous productions across the globe, but didn't easily confirm the location of the photo. So, I checked out each of the 7 venues and compared them to the newspaper photo.
More cyber defense! There are a bunch of open-source tools that can help scan, track, investigate
threats, like UrlScan.io, which scans for malicious URLs; Abuse.ch, which offers a suite of platforms
to tackle malware and botnets; PhishTool helps investigate emails; and Cisco's Talos Intelligence is a
platform for intel gathering. So, for example, if we have an email with a malicious attachment, we can
upload that to PhishTool, which will give us the associated SHA256 that we can then enter into Talos
File Reputation, which will in turn give us the malware family and other detection aliases.
Another tool is Yara, which can identify malware based on binary and textual patterns (that is,
hexadecimal numbers and strings). Cuckoo and Python's PE Module help generate Yara rules and others,
including a whole suite of Norse-themed tools like LOKI, THOR, and FENRIR, add a lot more firepower.
Detour into hexadecimal aka base 16 aka hex:
Hexadecimal is a numbering system with base 16 and it's one of four numbering systems; the others are
decimal (base 10), binary (base 2), and octal (base 10). The hexadecimal system contains 16 sequential
numbers as base units, including 0. The first nine numbers (0 to 9) are the same ones commonly used in
the decimal system. The next six two-digit numbers (10 to 15) are represented by the letters A through
F. This is how the hex system uses the numbers from 0 to 9 and the capital letters A to F to represent
the equivalent decimal number. We need hexadecimal numbers, which arrange binary numbers into groups
of four bits, to manage binary string equivalents of large decimal numbers. Hex numbers are more
compact because they can represent large binary numbers with fewer digits, which makes them easier to
understand.
Back to cyber defense!
The Cyber Kill Chain framework,
established
in 2011 by Lockheed Martin, is designed for identification and prevention of the network intrusions;
its assertions that "it is possible to anticipate and mitigate future intrusions based on knowledge of
the threat" and "the principle goal of campaign analysis is to determine the patterns and behaviors of
the intruders, their tactics, techniques, and procedures (TTP), to detect 'how' [and 'why'] they
operate rather than specifically 'what' they do" make it the spiritual precursor for the MITRE ATT&CK
framework.
"Early evolutions of threats to computer networks involved self-propagating code. Advancements
over time in anti-virus technology significantly reduced this automated risk...To date, most
organizations have relied on the technologies and processes implemented to mitigate risks
associated with automated viruses and worms which do not sufficiently address focused, manually
operated APT intrusions. Conventional incident response methods fail to mitigate the risk posed by
APTs because they make two flawed assumptions: response should happen after the point of
compromise, and the compromise was the result of a fixable flaw"
The
Unified Kill Chain
was created in 2017 and updated regularly to complement the Cyber Kill Chain, which at this point is
over a decade old, and ATT&ACK, which is time-agnostic. The Unified Kill Chain breaks 18 tactics (all
of which are covered in ATT&CK) into three progressions:
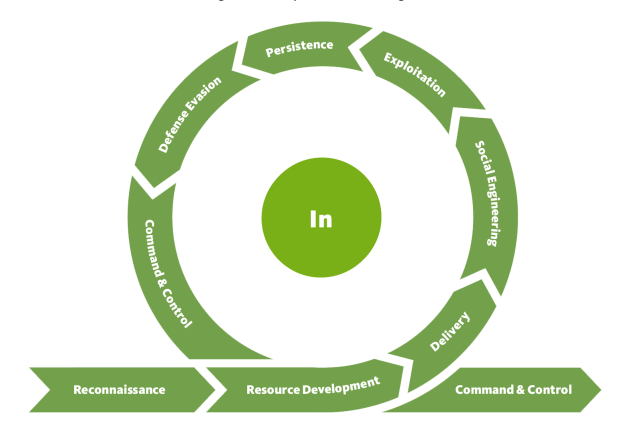
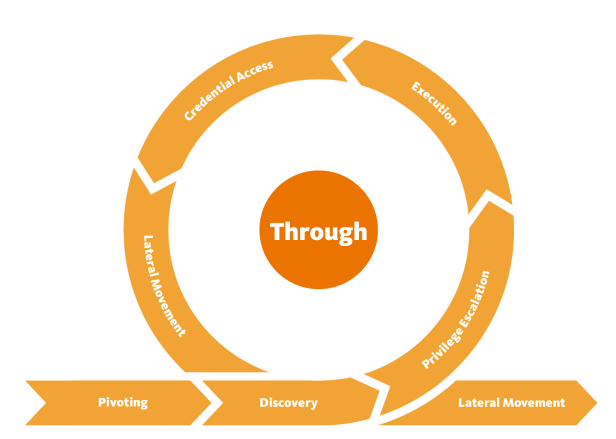
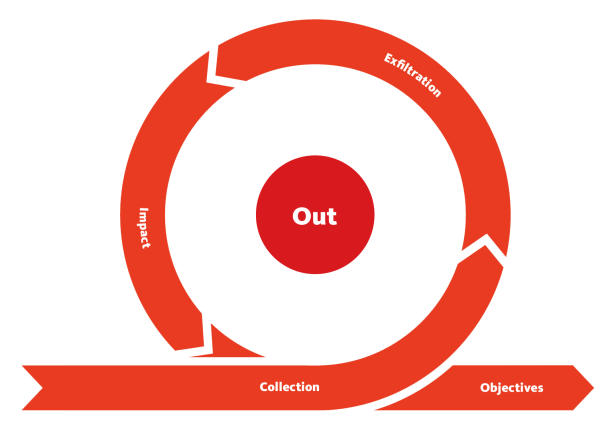 And it makes the point that attackers need not pass through each stage of the Cyber Kill Chain: "in
individual attacks, some tactics may occur out of their expected sequence or be bypassed altogether."
And it makes the point that attackers need not pass through each stage of the Cyber Kill Chain: "in
individual attacks, some tactics may occur out of their expected sequence or be bypassed altogether."
The
Pyramid of Pain
is a diagram created in 2013 that "shows the relationship between the types of indicators you might
use to detect an adversary's activities and how much pain it will cause them when you are able to deny
those indicators to them." (Quite frankly, I think it gets itself confused about whether the pyramid
on from the attacker's or the defender's perspective and it doesn't compare like with like. It tries
to do too much and gets a little tangled.)
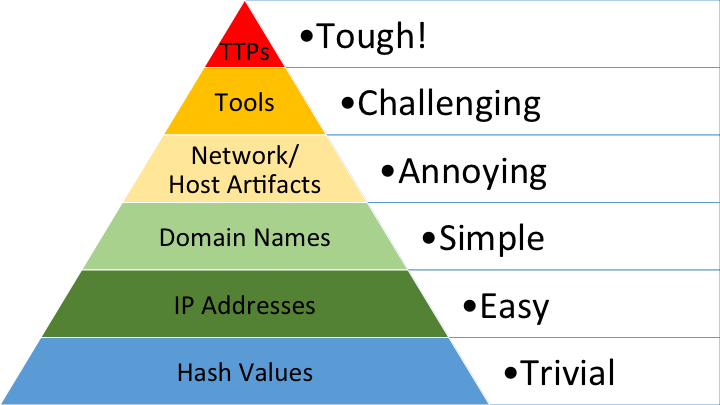
A
hash value
is a numeric value of a fixed length that uniquely identifies data and is the result of a hashing
algorithm, such as MD5, SHA-1, and SHA-2. Hash values form the base of the pyramid, meaning that
finding hash values is an indicator of malicious activity and that disrupting an adversary's hash
values will inflict trivial pain to them. These hashes can reflect a malware sample or a malicious
file and can be used as a way to uniquely identify and reference a malicious artifact, and various
online tools can be used look up a hash, like VirusTotal and Metadefender Cloud-OPSWAT. But, it's so
easy for an adversary to change a hash value, and there are so many of them around, that in many cases
it may not even be worth tracking them.
IP addresses
are used to identify any device (a desktop computer, a server, a CCTV camera, etc) connected to a
network. Knowing an adversary's IP address is valuable, and many open-source databases like Cisco
Talos Intelligence, provide reputation and location checks for IP addresses. Defenders can block,
drop, or deny particular inbound requests, but it's unfortunately again pretty trivial for an
adversary to simply switch to a new IP address or use
Fast Flux,
a DNS technique that makes identifying the communication between malware and its command-and-control
server challenging.
Domain names
are a bit more of a pain for an attacker to change because they would most likely need to purchase and
register the domain and modify DNS records. The availability of DNS providers with lax registration
standards and low costs make it relatively simple to change domain names. Attackers often try to hide
malicious domains under URL shorteners or - less often because browsers are pretty good at unmasking -
by using Puny code, which is a way of converting words that cannot be written in ASCII into a Unicode
ASCII encoding. Fortunately, there are
ways
to preview the full url of a shortened url: by adding "preview" or "+" to the url or you can using a
url checker.
Host artifacts
are the traces or observables that attackers leave on the system, such as registry values, suspicious
process execution, attack patterns or IOCs, files dropped by malicious applications, or anything
exclusive to the current threat.And a
network artifact
can be a user-agent string, C2 information, or URI patterns followed by the HTTP POST requests. A
network artifact can be detected by packet-capture analysis (PCAPs) by using a network protocol
analyzer or exploring IDS(intrusion detection system) logging.
Tools
are what they sound like: the tools used by defenders and adversaries. And finally,
TTPs
are the whole puzzle: if you can detect and respond to the TTPs, you're in good shape.
We practiced the very first teensy step a pentester would take when reviewing an application. Using only the in-built browser tools, we hunted for sensitive information left in the frontend code, looked for known bugs about the framework version used, poked around in directories we could access, and inspected the JavaScript and GET/POST requests. (A breeze for anyone with programming experience!)
Finished up the React random color generator app (check out the repo here)! My original idea was to refactor a lot of legacy Codecademy code, but I decided it made more sense to just build a new version myself using current best practices. And turns out my version, which uses React Hooks, only needs about half the lines of code that the Codecademy version did. So it was a perfect way to really see the utility of Hooks in practice! It also helped me understand that State can be a number of things (a boolean, a string, an operator) and that State can do more than a single thing at once - in this case, it changes both the background color and the visibility of some text.
It's also time to dip my toes back into algorithms. Not only is it appropriate to group them with my
other favorite brain teaser, Arabic, their histories are intertwined!
While Europe was struggling through centuries marked by varying degrees of murk (I love that some
scholars hate calling the post-Roman era the "Dark Ages"), the Muslim world was enjoying a golden age
of science, culture, and economics. One of the resident scholars in Baghdad's House of Wisdom,
Muhammad Ibn Musa al-Khwarizmi, wrote a treatise on the Hindu-Arabic numeral system in the 9th
century, and the word
algorithim
is a mangled Latinization of his name. (He is generally known for
revolutionizing
algebra and arithmetic.)
So I figured I'd just start with translating some easy conditionals from Ruby to JavaScript.
n = 10
if n == 10
p 0
else p -1
end
let number = 3;
if (number === 10) {
console.log(0);
} else {
console.log(-1); }
While I was at it, I learned how to ask a user for input in JavaScript via the browser console. So, the equivalent of Ruby's
puts "Enter a word:"
word = gets.chomp
if word == "marco"
puts "polo"
end
is
var word = window.prompt("Enter a word:");
if (word === "marco") {
console.log("polo");
}
التعلُّم
I realized my commits to this GitHub Page weren't showing up on my profile, so I braved posting in the
GitHub Community forum. I was pleasantly surprised by the speedy and accurate
help
I received! Turns out some errant quotations around my otherwise correct email address were to blame;
although I'm still not sure why that's not the case for my other repos.
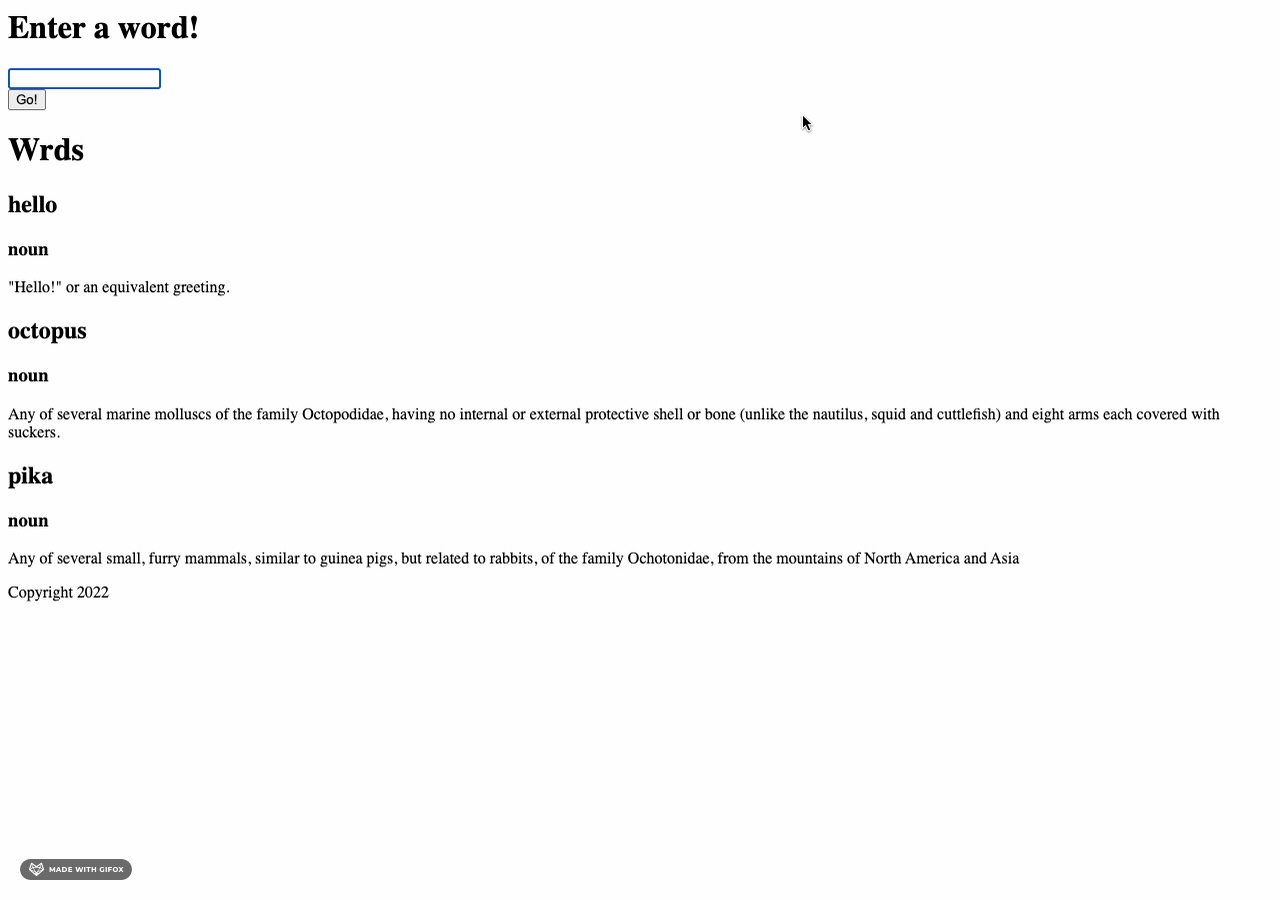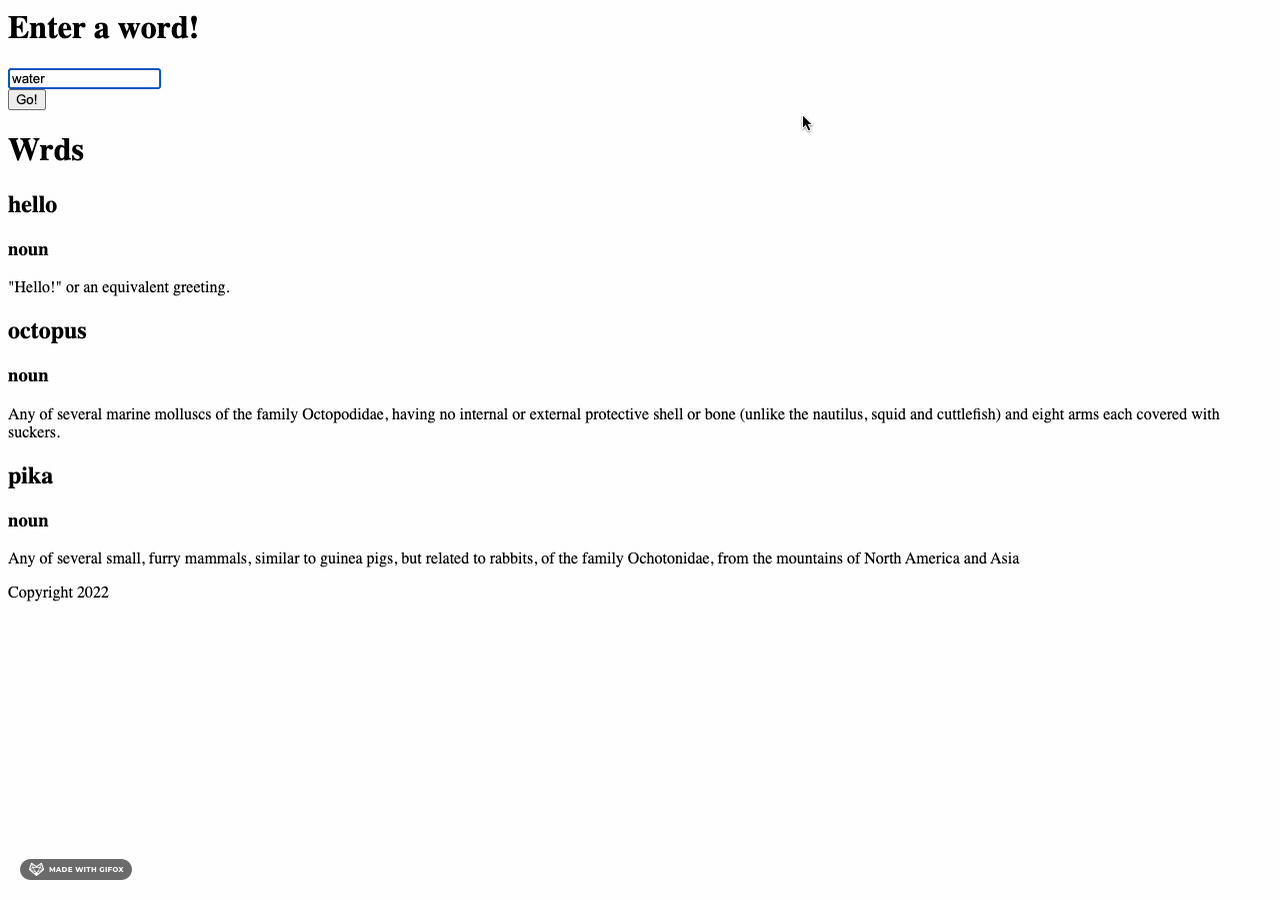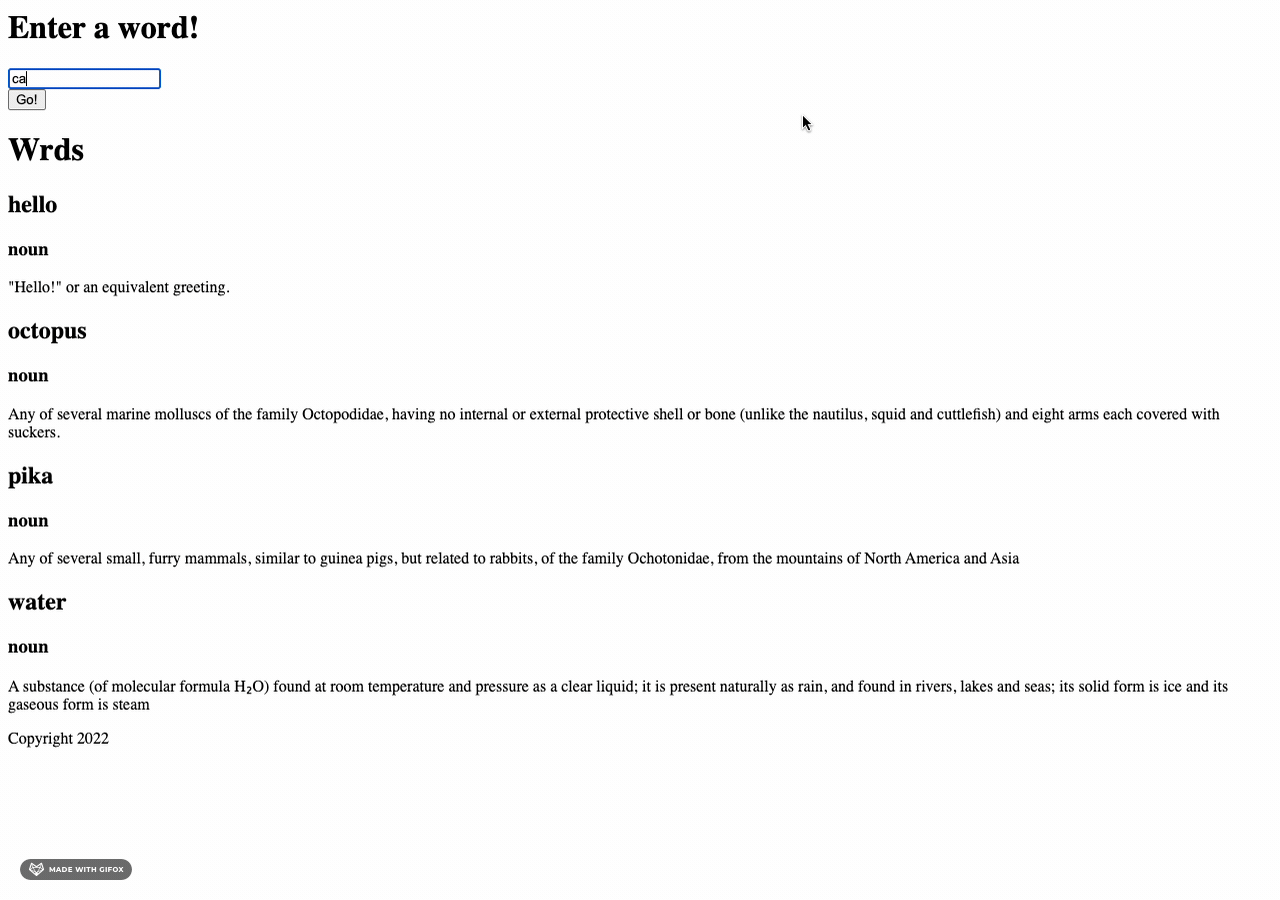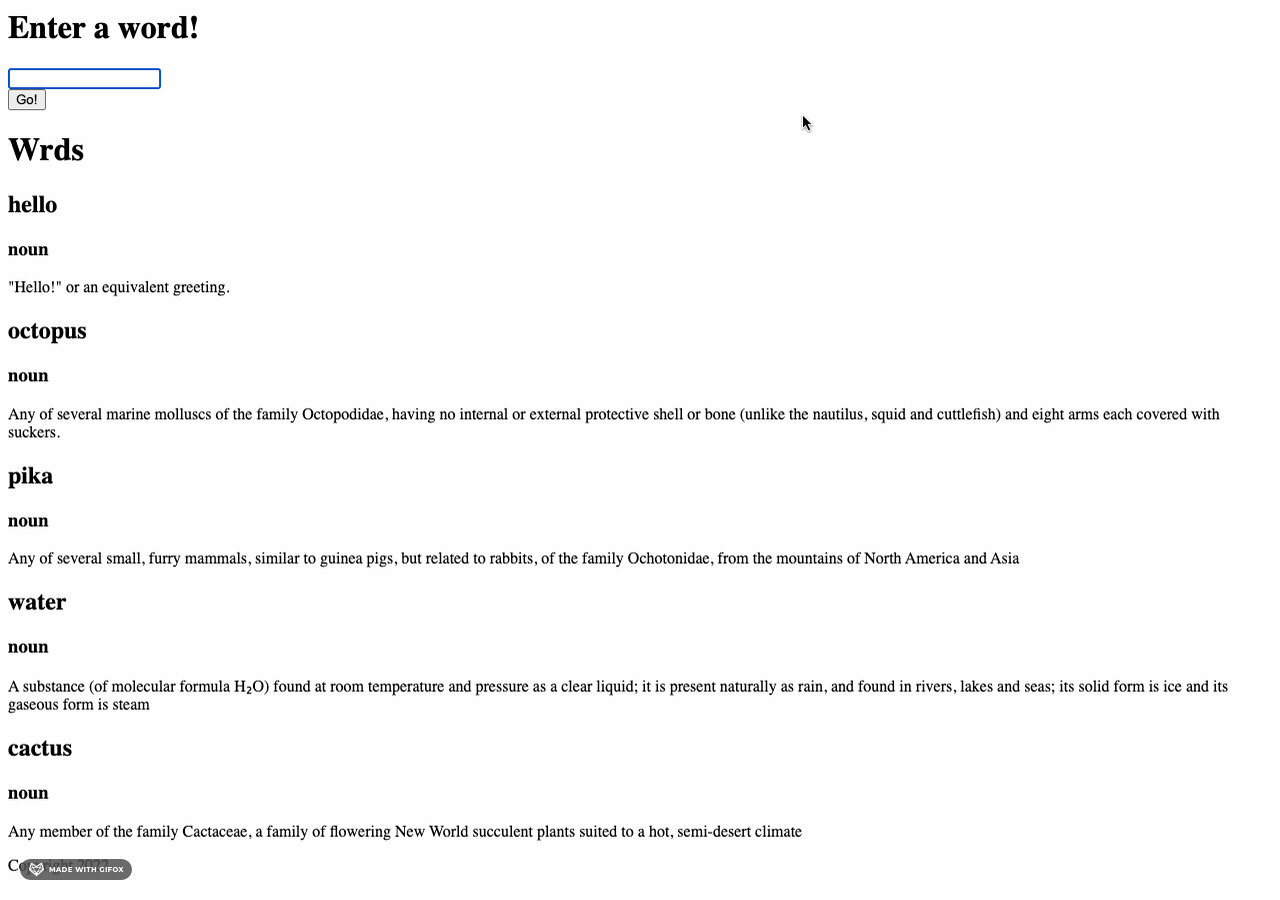
I built on my search bar trials from the other week to start one for the entire blog. I wrapped all my
content in an unordered list, removed the bullet styling with
style="list-style-type: none"
and created a new JavaScript function to match.
The way it's currently coded, a user will see the weekly entry that includes their entered search term
and all other entries will appear as empty boxes.
Next up will be figuring out how to highlight a particular search term.
System Configuration is the place to start for many helpful advanced tools. For example, System Configuration > Computer Management > Event Viewer will display a record of the computer's activity and is helpful for diagnosing problems and investigating actions executed on the system. And of course docs matter for cybersecurity just as much as they do for any sort of programming! The Microsoft docs tell us exactly what events will be logged here.
ATT&CK is a free, open, and globally accessible knowledge base of observed adversary behaviors. ATT&CK
focuses on the TTPs (the tactics, techniques/sub-techniques, and procedures) executed by adversaries.
It was developed to document and understand adversary behaviors, it is built from publicly reported
cyber activity, and it connects TTPs to the threat actors and malware/tools that perform them. Those
relationships are captured in the ATT&CK matrices. ATT&CK creates a common language for security
practitioners and it can help us measure defenses against real adversary behaviors. ATT&CK Navigator
allows us to annotate these matrices to visualize, export, and share anything we're trying to capture
and present.
ATT&CK considers tactics to be the goals an adversary has during an attack (adversary objectives / the
"why"); it treats tactics as objects and has assigned each a unique ID. These tactics are the column
headers in the enterprise matrix.
ATT&CK defines techniques as the means by which adversaries achieve their goals (adversary behaviors /
the "how"). Sub-techniques are simply more specific; they always have a single parent and are often
specific to a single platform. They were created to capture innovations and changes of behaviors and
have a wealth of metadata like mitigations and detection. Technique IDs also have their own unique
identifiers and sub-technique IDs are extensions of their parent technique.
ATT&CK defines mitigations as configurations, tools, or processes that can prevent an adversary
behavior from working. And of course, mitigations also have their own unique IDs and they're mapped to
specific techniques.
ATT&CK data sources tell us what to collect (via sensors and logs, for example). ATT&CK detections
provide high-level strategies to identify a technique used by an adversary, essentially, a guide to
interpreting the collected data. ATT&CK groups are "clusters" of intrusion activity and software is,
well, what it sounds like: the tools/malware used by threat actors.
ATT&CK allows us to map adversaries to behaviors via techniques and sub-techniques and references the
publicly available cyber threat intelligence about these behaviors.
التعلُّم
Adding a search bar to my blog prompted me think about adding in some security to prevent malicious
use. My original search bar didn't allow a user to write HTML to the page, so something like this
wouldn't actually work:

But of course it's a best practice to sanitize any and all user input to prevent HTML or JavaScript
injections to redirect browsers, steal information, or conduct Cross-Site Scripting (XSS) attacks. I
thought that this might be another classic case of regex to the rescue, but turns out there are some
very salty opinions
against it. So I used
DOMPurify
instead:
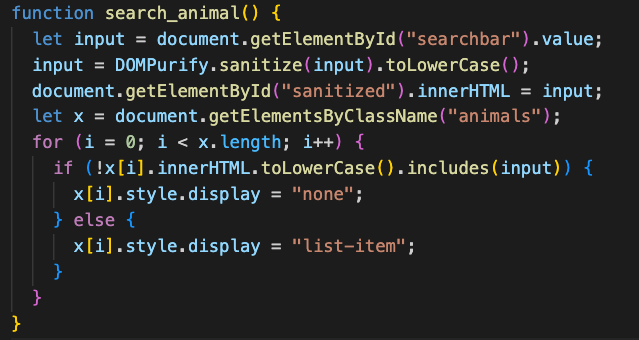
To work, DOMPurify needs to write HTML into the DOM element, so I had to add an
.innerHTML
method that ties back to a placeholder
div
in the HTML.
التعلُّم
A network is just interconnected devices. The end! It's fascinating that everything we do, every day,
relies on that not-so-simple statement. And for some reason, the typical liberal arts education
ignores the centrality of networks, not only to the human experience, but to international relations
(IR) and governance. This is for another day, but I think we're missing out on some very neat
interdisciplinary connections, like the fact that today the internet operates largely without massive
international government support or intervention.
I imagine liberal arts prefers to keep networking in a safe silo because it's complicated and yet
still concrete; we're not at liberty to create models and argue about how it actually works (looking
at you, economics).
Anyway, every device that can be connected to a network - a phone, a computer, a wireless speaker -
has a MAC (Media Access Control) address and, once connected, an IP address. A MAC address is unique
to each device and IP addresses can change from device to device, although they cannot be active
simultaneously more than once within the same network. The protocols - a set of standards (not
developed or maintained by any government-level entity, IR!) - IP addresses follow are the backbone of
networking and enable devices to communicate.
Networks can be different sizes and span different geographical breadths. LAN is just a local area
network, for example. But then it starts to get confusing (and this is probably where IR jumps
overboard). There are a couple different models to describe
how
a network works and then even within a single type of network there are different topologies. Let's
start with the models, which break networking into different layers to categorize the different,
complicated functions that are responsible for specific tasks. Most humans are really only familiar
with
part
of one layer, the application layer (which is either one of seven layers in the OSI model, which is a
conceptual, neutral model, or one of four in the TCP/IP model, which specifically refers to how the
current Internet works): we use GUIs to send requests and receive data. I don't even know if that
counts as the tip of the iceberg; maybe it's just the initial snowfall on a glacier hundreds of years
before a chunk of ice calves into the sea.
Ok, so still within that application layer, we rely on network protocols to get the data transferring.
The Domain Name System (DNS) protocol converts domains to IP addresses, IMAP/POP/SMTP handle email,
and the Hyper Text Transfer Protocol (HTTP) handles our web requests to servers (and make our
applications' basic CRUD actions work). Opening the network tab in developer tools shows how many HTTP
requests are required to load a single specific website:
Secure Shell (SSH) protocol enables access to a remote terminal or virtual machine over a secure
connection, File Transfer Protocol (FTP) does just that, and Server Message Block (SMB) protocol
allows users to interact with a remote system like a file share or printers.
And then super important protocols like TCP and UDP live in the TCP/IP model's transport layer - and
we haven't even talked about the other layers!
Once again, the key to this kind of interactivity is the Javascript method
getElementById,
which grabs the relevant HTML (in this case, the HTML with an id of "searchbar"). This time, we'll
also call
.value
to capture the actual content of what a user types into the searchbar, not just the HTML element.
 And we'll use
And we'll use
getElementsByClassName
to loop over the relevant content to see if the user's input matches anything.
التعلُّم
Sofia Santos - OSINT Exercise #006:
A
TinEye
reverse image search yielded 377 exact results dating to at least 2006, confirming that the photo in
question is not from a January 2023 attack.
Sofia Santos - OSINT Exercise #002:
A
Google Lens
reverse image search easily pulled the text in the picture and identified the Flinders Street Railway
Station in Melbourne. Plugging the coordinates into Google Earth Pro and accessing the street view
feature provided a more accurate perspective of the tall structures in view, and a simple Google
search yielded the heights for the buildings in question (although, of course, the first Google hit
was for something else 😛).
Completed THM's
Searchlight IMINT room,
which was created by one of the (now-former) OSINT Curious members. Good imagery intelligence, or
IMINT, analysis starts with methodically decomposing the image and focusing on the context,
foreground, and background, noting any particular things like signs or landmarks along the way. The
hardest part of this particular challenge was identifying the photographer of a particular image; the
image didn't show up in my reverse image searches, so I looked at an embedded map in the official city
tourism page and found it there. We also experimented with
FFmpeg
, a tool to parse and process videos, although for this (relatively easy) exercise I found Google
Earth Pro to be equally useful.
I wanted brush up on my Linux because it's been a few weeks since I followed
Michael Bazzell's
instructions to create Linux virtual machines and install a bunch of OSINT tools.
Linux is simply another operating system, like your Mac or Windows OS, except that it's not subject to
the same restrictive licensing. Linux's open-source nature makes it free and customizable for specific
purposes, such as cybersecurity. Linux is also present in our daily lives - it serves as the OS for
many IoT devices.
For today's project I practiced using SSH (secure shell) connections to hook up to the command line of
a remote Linux machine and I revisited some commands that I don't use on a daily basis in my other
programming endeavors:
echo
repeats anything we type and in concert with operators can be a shortcut to create new files with
content
whoami
finds out what user we're currently logged in as
cat
spits out the contents of a given file
find
looks for specific file names, wildcards (e.g.,
find -name *.txt
)
grep
searches the contents of files for specific values
file
outputs a file's type
su
switches user
ls -l
shows file permissions
ps aux
shows running processes
less
shows a file's contents one page/screen at a time
التعلُّم
أداة لتنظيم ملفات الصوت والفيديو وجعلها قابلة للبحث 🧿 A tool for organizing sound and video files and making them searchable
أول كأس عالم لجمع القمامة في اليابان..من البلد العربي الوحيد المشارك؟ 🧿 The first world cup to college garbage in Japan. Who is the only Arab country participating?
I wanted to tackle a project that would help me really understand React Hooks and what they were
designed to do, so I decided to refactor some
old Codecademy code
that uses classes rather than functions and repetitive component lifecycle code like
componentDidMount
and
componentDidUpdate.
Or, in English, today's best practices use different JavaScript syntax to create the code that serves
as the fundamental building block for something that performs a
task.
And "component lifecycle code" is essentially how React gets your code onto the webpage, and the
syntax for doing that has also changed.
I simplified the project to start. I'll eventually turn this into a random color generator, but for
now I'm just going to create a button that changes its background color when clicked. I did something
similar with the
animal facts app,
but in that case I just manipulated the DOM directly via
document.getElementById.
This time we're going to do it the right way by using state. The funny thing is that I've used all
these concepts in more sophisticated ways before, particularly with
SomeTrails,
but it takes doing and unpacking several times to really internalize it.
التعلُّم
رئيس الاتحاد الفرنسي لكرة القدم يستقيل من منصبه بعد مزاعم بالتحرش الجنسي 🧿 The president of the French Football Federation resigns after allegations of sexual harassment
روسيا وأوكرانيا: تحطم طائرة بدون طيار بالقرب من موسكو في هجوم تصفه روسيا بأنه "فاشل 🧿 Russia and Ukraine: A drone crashes near Moscow in attack Russia calls 'failed'
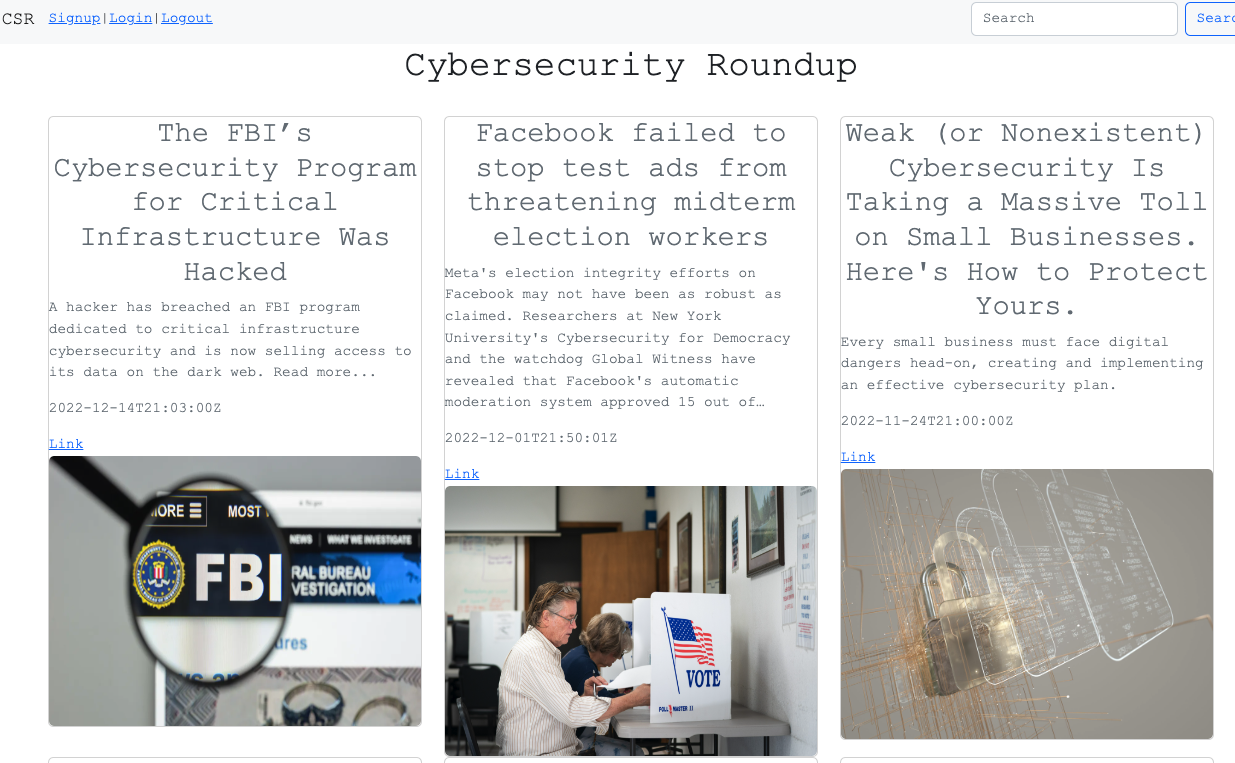
In future updates I'll be replacing craftings/learnings with thematic buckets to better delineate my 🌵 wildly 🌵 different projects.
onClick
and took a deep dive into
JavaScript's capabilities to manipulate the HTML DOM.
getElementById
to access specific HTML elements, and then I used a couple different properties to do different things,
like replace the content of HTML elements (
innerHTML
) or change the value of an HTML attribute (
.attribute
).


التعلُّم
"في تونس، سلسلة اعتقالات تؤكد "الوصول إلى نقطة اللاعودة 🧿 In Tunisia, a series of arrests confirms 'reaching a point of no return'
زلزال يضرب طاجكستان على الحدود مع الصين بقوة 7.2 درجة 🧿 A 7.2 magnitude earthquake hits Tajikistan along its border with China.
ReactDOM.render()
), and figured out how to translate it all into an app that I could locally host.
Decision-making moments are where well-built teams shine. Teams help to limit the effects of adverse human factors on our choices and make sure our actions remain in line with our team mindset and terrain-use plan...Cultivating backcountry teams with a shared vision and approach gives us confidence that our teammates will respect each other's opinions, perspectives, and feelings as we plan and execute backcountry experiences together. We understand that this is how we rely on each other to enjoy the backcountry, and how we live on to cherish the memories we create together in the mountains. Teams work best when we give each other the courage to speak up and listen.


1.upto(number_of_dice) do
. I did, however, manage to break the gameplay... 😛
And! Finally finished this little dragon! Time to send him off to an excited little baby!

input type="text" id="uname" name="uname" pattern="[a-zA-Z0-9]+"
will filter for a case-insensitive alphanumeric string.
@tasks.select { |task| !task.completed }
.
/\D/.match(isbn_string.chop)
.
grep
-- which, turns out, stands for global/regular expression/print. Here's a nifty
link
about finding things using the command line.)
nokogiri
because my KML file is actually primarily composed of XML and HTML. I tested my code to print the doc to
the terminal and for some reason it only pulled a small portion. It did, interestingly, include more
DOM-like features than were visible in the KML file I was working with in in TextEdit.
nano
to get a sense for the data in a log file,
wc -l
to get the number of lines in it, and
grep
, which finds and prints lines that match a pattern, to search.
elsif sentence == sentence.upcase && sentence.include?("ABCDEFGHIJKLMNOPQRSTUVWXYZ")
but there's gotta be a better way.
items = { "chair" => 100, "book" => 14 } hash = {} items.each do |name, price| hash[name] = price end
p hash # {"chair"=>100, "book"=>14}
Computers may be as close as we get to magic in the real world: we type incantations into a machine, and — if the incantations are right — the machine does our bidding. To perform such magic, computer witches and wizards rely not only on words, but also on wands, potions, and an ancient tome or two. Taken together, these tricks of the trade are known as software development: computer programming, plus tools like command lines, text editors, and version control.